Access control system (ACS) is a control system that adopts modern electronic technology and software information technology to identify the target through correct identification at the entrance and exit, determine the release or rejection of the target, and perform operations such as recording and alarming at the same time. Entry and exit numbers, entry and exit times, and entrance/exit numbers are registered and stored to ensure the security of controlled areas and targets and intelligent management.
Entrance and exit control system
Entry and exit control systems are widely used in smart building security, vehicle management, logistics management, security, banking and other fields.
The goals of control include people and things. In the intelligent building security management system, the main control is the person. This system is usually called the access control system. This article focuses on the different identification technologies in the intelligent building entrance and exit control system.
The composition of the entrance and exit control system
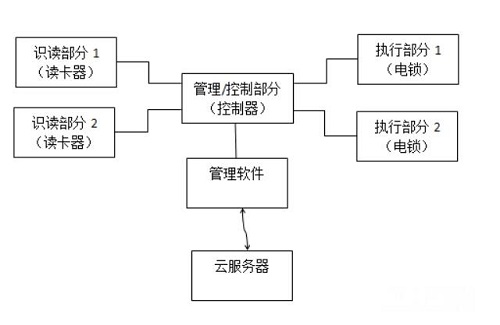
The entrance and exit control system is mainly composed of a reading part of the identification mark, a management/control part, an execution part, a transmission part, a corresponding management software, and a cloud server. The typical system is as follows:
The entrance and exit control system has a variety of construction modes. According to its hardware configuration mode, it can be divided into integral type and split type; according to its management/control mode, it can be divided into independent control type, network control type and data carrier transmission control type.
All components of the integrated entry and exit control system are internally connected, combined or integrated to realize all the functions of the entrance and exit control.
The various components of the split-type entrance and exit control system have separate parts in structure and parts that are combined in different ways. The separate and combined parts are connected together as a system through electronic, electromechanical and other means to realize all the functions of the entrance and exit control.
Independent control type entrance and exit control system, all functions of its display/programming/management/control of the management/control part are completed in one device (entrance controller).
The networked control type entrance and exit control system does not have all the display/programming/management/control functions of its management/control part completed in one device (entrance controller). Among them, the display/programming function is completed by another device. Data transmission between devices is achieved through wired and/or wireless data channels and network devices.
Reader's classification and characteristics
The goal of the control system of the entrance and exit control system in the intelligent building is the crowd. It belongs to the security system. The reader is used to identify whether the personnel have the right to enter or exit. The reader collects the input data and compares it with the data stored in the controller or server. , The data is released when it is consistent. Commonly used readers have the following types:
1) Password type:
Password recognition: Identify the person's access rights by checking whether the input password is correct. These products are divided into two categories: one is a common keyboard type, and one is an out-of-order keyboard type. The main features are simple equipment, easy to use, no need to carry cards, and low cost. The disadvantage is that the number of password groups cannot be too large, the password is easily leaked, and the security is very poor; the average person has no access to the record. Password-type access control is generally used in situations where the level of safety precautions is not too high.
2) Reader:
IC card is an integrated circuit card, which is an information carrier. The IC card stores information through the integrated circuit in the card and uses RF technology to exchange data with a card reader that supports the IC card. The IC card is currently the most widely used reading method in the entrance and exit control system. IS0 standard card size is 85.5×54×0.76mm
There are many kinds of IC cards, and there are many classification methods. According to the reading interface, the IC card can be divided into contact type and non-contact type; read-write mode can be divided into read-only card and read/write card; press reading distance can be divided into short-distance card and long-distance card; According to the power supply can be divided into passive cards and active cards.
A. Contact and non-contact:
The contact type IC card reads and writes data by contacting the contacts of the IC card reading and writing device with the contacts of the IC card. Non-contact IC cards and IC card readers have no circuit contact. They read and write through wireless technology's read/write technology. In addition to the CPU, logic unit, and memory unit, the card embedded in the card has an RF transceiver circuit.
In the intelligent building's entrance and exit control system, due to the high frequency of card swiping, the non-contact IC card is commonly used. It has the advantages of convenient use and high reliability, and is less used with contact type IC cards. At present, contact-type IC cards are mainly used for bank cards, which have the characteristics of convenient use and good confidentiality.
Currently, the most common non-contact IC card on the market is a logical encryption card. Stream cipher technology is used, and the key length is not very long. There are generally certain security risks and there is the possibility of being cracked by hackers. In some areas where high security requirements tend to use embedded microprocessor-based contactless CPU card chips, the CPU card chip has a double internal security mechanism, one is the chip itself integrated encryption algorithm module, the second is the CPU card chip unique The COS operating system and the national secret algorithm using domestic chips are not open to the public, so the secret algorithm is generally more secure than other public algorithms.
B. Read-only card and read/write card
A read-only card is also called an ID card and can only read the card number information. The read-write card can read information in the card as well as write operations to the card, and can write information such as the authority, validity period, and amount. Read and write cards are widely used in smart access control, city bus card, campus card and so on. At present, mobile purses are used in Shenzhen and other places. You can use credit card to spend and take public transportation. Actually, IC cards and mobile phone SIM cards are combined together. This is different from the NFC mentioned later in this article. Read-only card readers are far from reading and writing cards, and they are also used in smart access control systems.
C. Long distance card
Ordinary IC card reading distance in the 2-10cm, the general reading and writing distance of 1 meter or more is called a long-distance card, long-distance can be divided into passive cards and active cards. Long-distance cards generally use radio frequency identification (RFID) technology, referred to as RFID, and the sensing distance is controlled within 3 to 10 meters. Due to the long sensing distance and fast recognition speed, it is mainly used for vehicle access management and automatic charging.
3) Near Field Communication Technology NFC
Near Field Communication Technology (NFC) is an integrated evolution of non-contact RFID technology and interconnection technology. NFC devices integrate inductive readers, proximity cards and point-to-point functions on a single chip. Can identify and exchange data with compatible devices within a short distance. The working distance is within 10cm and the working frequency is 13.56MHz. At present, smart phones basically have NFC function.
NFC has three operating modes: Card emulation, P2P mode, and Reader/writer mode. NFC technology is used in the entrance and exit management system to use the card emulation mode. This mode is actually quite equivalent. For an IC card using RFID technology, users can present their NFC-enabled smart phones just before accessing the card reader. In this mode, swiping cards can be opened even if the phone is not powered.
NFC technology is mainly used in mobile payment, identity recognition, entrance control and other occasions. With the popularization of smart phones and mobile payment being accepted by consumers and merchants, the application of NFC technology will become more and more extensive.
4) Biometrics
Biometric technologies include fingerprints, irises, faces, palms, veins, and DNA. Fingerprint recognition has become one of the most widely used identification technologies and has become almost universal, due to its low system cost and ease of use. Synonymous with feature recognition. In addition, face recognition technology has also developed very rapidly at this stage, and fingerprint recognition and face recognition are mainly used in intelligent buildings.
A. Fingerprinting
Fingerprint refers to the ridges on the frontal skin of the human finger. The lines are regularly arranged to form different patterns. The starting point, the ending point, the joining point, and the bifurcation point of the ridge line are called detailed feature points of the fingerprint.
Fingerprint recognition refers to the automatic recognition by comparing the detailed feature points of different fingerprints. Because each person's fingerprint is different, the fingerprint between the same person's ten fingers also has obvious difference, and the fingerprint remains intact for life, so the fingerprint can be used for the automatic identification of the identity.
Fingerprint recognition has the characteristics of convenient use, fast recognition speed, low price, etc. The miniaturization of the fingerprint collection head has brought convenience to the integration of fingerprint recognition and opened up a broad application market. At the same time, there are some problems in fingerprint recognition; some people or some groups have few fingerprint features and are difficult to image; the user's fingerprints are left on the fingerprint collector head, and these fingerprint traces are used to copy fingerprints. Security issues.
Fingerprint recognition is now mainly used for access control and corporate attendance. With the development of smart homes, fingerprint locks have begun to enter home locks.
With the miniaturization of the fingerprint collector, the fingerprint recognition technology is integrated into the visual intercom system unit of the smart community to facilitate the entry and exit of the owners.
B. Face recognition
Face recognition uses the computer application technology of analyzing and comparing facial organ shape and position feature information to identify the identity, and it belongs to biometric recognition technology. At present, face recognition has become a research hotspot in the field of pattern recognition and artificial intelligence.
The main processes of face recognition are: face image acquisition and detection, face image preprocessing, face image feature extraction, and matching and recognition. There are many face recognition algorithms. The commonly used algorithms are: face recognition based on geometric features, face recognition based on the entire face image, face recognition based on connection mechanism, and recognition based on three-dimensional data.
Compared with other identification methods, face recognition has the characteristics of non-contact, non-mandatory, and concurrency, so the face recognition technology has important application value. In the intelligent building entrance and exit control system, it is mainly used in places such as access control, attendance, and airport security inspection. It is generally used in combination with other identification methods, such as being integrated in the door phone of a video intercom unit.
The change of ambient light around the face, the similar face, the obstructions of the human face, the aging of the face, and the face shaping may affect the accuracy of the recognition and improve the accuracy of the system by artificial intelligence compensation. It should be noted that the face recognition system must correctly identify whether the camera is in front of a real person or a photo. In order to prevent users from using photo fraud, improve system security.
5) Other readings:
In recent years, China has implemented the "Internet +" national strategy. The construction of smart communities is in the ascendant. The development of mobile Internet technology has spawned emerging identification technologies.
A. Mobile phone APP recognition
Access control unlock APP is installed in the smart phone, and the corresponding access control icon can be unlocked. The recognition of the mobile phone APP actually identifies the MAC code of the mobile phone, and the owner's identity information is bound with the mobile phone to achieve the identity verification. The smart phone accesses the cloud platform server through WIFI or mobile network (4G) to exchange data and confirm identity, and can realize local door opening and remote door opening. Therefore, it is also called “cloud door banâ€.
Community service APPs that are popularized in the community, most of the community O2Os are bound with door lock unlocking functions in order to increase the user's viscosity.
B. Two-dimensional code identification
The mobile phone APP recognition is generally used by owners or fixed customers, and does not apply to the identification of visitors. Therefore, a mobile phone two-dimensional code recognition technology is generated. The owner’s smart phone can generate two-dimensional codes and send them to visitors through social tools such as WeChat. Visitors can open the door and pass the two-dimensional code they receive at the access control entrance. The two-dimensional code can be set to be used on a time basis or on a per-use basis, expired and invalidated, which can improve the security of the system.
Conclusion
There are many kinds of readers for intelligent building entrance and exit control systems, and emerging reading methods are also emerging. You can select one or more reading technologies based on the actual situation of the project. A reasonable choice of reading methods can increase the cost-effectiveness of the system. Users are safer and more convenient to use.
We can provide you the realiable quality and best price truck parts to maintance your after market service suitable for the BEIBEN truck. Our main product:
- cabin assy and cabin accessory; Headlamp, taillamp, bumper, front cover, door and glass;
- Chassis Parts; sun gear, brake pad, clutch plate, bearing, differential, PTO, and axle;
- transmission parts; transmission shaft, universal joint, steering pump, clutch booster and brake pedal;
- Engine Parts; cylinder liner, piston, piston ring, oil seal, connection rod bearing, starter, injection pump, oil pump, water pump, air filter, oil filter and fuel filter;
- other spare parts. Curtain, roof, water tank, radiator, inter cooler and ect.


Beiben Truck Parts
Beiben Truck Parts,Truck Body Parts,Beiben Truck Spare Parts,Beiben Truck Engine Parts
Jinan JF Co., Ltd , https://www.jfsinotruk.com